Thank You for a Strong Year
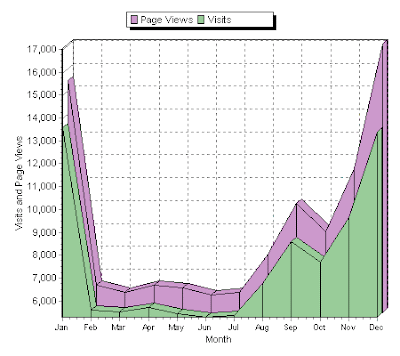
The image above comes from my Sitemeter blog statistics page. I'd like to thank all of my readers for making the TaoSecurity Blog part of their Internet experience. We've had about 337 posts this year, on a range of subjects. Our two year anniversary will happen January 8th. I'd also like to thank those of you who have been reading my Amazon.com book reviews and voting them "useful." I receive no monetary compensation for any book reviews done at Amazon.com or here, but I do like seeing positive feedback on my reviews. I hope to keep blogging and reviewing as I begin work on my next book , tentatively titled Extrusion Detection: Network Security Monitoring for Internal Intrusions . I'll post information on Extrusion Detection once I have an ISBN, but I expect it to hit bookshelves in the fall. My collaboration with Keith Jones and Curtis Rose called Real Digital Forensics should appear on bookshelves in the summer. 2004 has been a great year, especi...





