Continuous Diagnostic Monitoring Does Not Detect Hackers
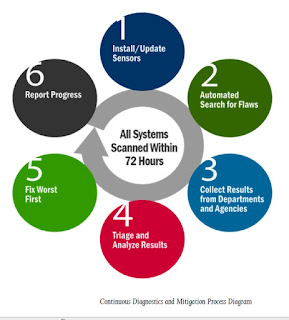
There is a dangerous misconception coloring the digital security debate in the Federal government. During the last week, in the wake of the breach at the Office of Personnel Management (OPM), I have been discussing countermeasures with many parties. Concerned officials, staffers, and media have asked me about the Einstein and Continuous Diagnostic Monitoring (CDM) programs. It has become abundantly clear to me that there is a fundamental misunderstanding about the nature of CDM. This post seeks to remedy that problem. The story Federal cyber protection knocked as outdated, behind schedule by Cory Bennett unfortunately encapsulates the misunderstanding about Einstein and CDM: The main system used by the federal government to protect sensitive data from hacks has been plagued by delays and criticism that it is already outdated — months before it is even fully implemented. The Einstein system is intended to repel cyberattacks like the one revealed last week ...


