Thank You for Another Great Year
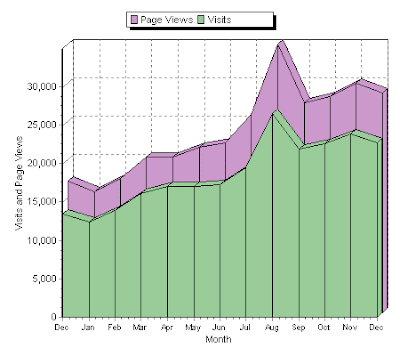
Exactly one year ago today I posted a thank-you note for the great year of blogging in 2004. A look at the 2004 statistics shows as recently as July 2004, this blog had less than 6,000 visitors per month, as tracked by Sitemeter . I have no idea how Atom, RSS, and other republishing is affects those statistics. Soon after my first book was published, we broke through the 10,000 per month mark and have never looked back. As you can see from the 2005 chart above, we're at the 22,000 per month mark now, and broke through 25,000 in August during my coverage of Ciscogate . This blog continues to be a nonpaying venture, despite offers to commercialize, syndicate and repackage the content elsewhere. Others already do this without my permission, but I thank those more responsible people who ask before posting my content elsewhere. For example, I've given the great publisher Apress blanket permission to quote anything I say here. This is my small way to say thank you for th...


