Why UTM Will Win
We know how many words a picture is worth. The figure at left, from Boxed In by Information Security magazine, shows why Unified Threat Management appliances are going to replace all the middleboxes in the modern enterprise. At some point the UTM will be the firewall, so the gold UTM box above will also disappear. In some places even the firewall will disappear and all network security functions will collapse into switches and/or routers.
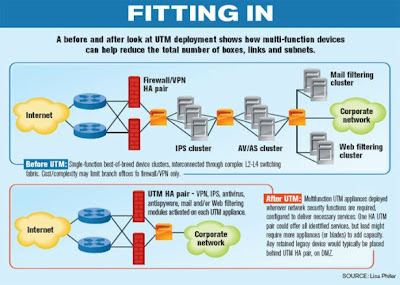
I'd like to show one other diagram from the story.
Just because I think this is going to happen (or is happening -- look at what your Cisco router can do) doesn't mean I like it. The more functions a box performs, the greater the likelihood that all of those functions will be performed at a mediocre level. Mediocrity is an improvement over zero security protection for some sites, but elsewhere it will not be sufficient.
I should say that the top diagram has its merits, with simplicity being the primary advantage. With so many networks having multiple "moving parts," it can be tough to stay operational and understand what's working or not working. Moving all those moving parts onto a single platform may not yield all the simplicity one might expect, however!
One way to address the weaknesses of these UTMs is to deploy stand-alone devices performing network forensics, so they record exactly what happens on the network. Using that data, one can investigate security incidents as well as measure the effectiveness of the UTM. I do not foresee network forensics collapsing into security switches/routers due to the data retention requirements and reconstruction workload required for investigations.
To survive I think network security inspection/interdiction vendors either need to be in the "meta-security" space (SIM/SEM) or in the do-it-all space (UTM). If your favorite vendor is in neither space, expect them to be acquired or go out of business.
I'd like to show one other diagram from the story.
Figures like these, showing which products and their "features," are another reason UTM will replace point product middleboxes. "Hey, I read in this magazine that product X checks 7 boxes, but product Y only checks 3. Let's look at product X." These are the sorts of figures that people who are not security experts and are not interested in or capable of assessing security products like.
Just because I think this is going to happen (or is happening -- look at what your Cisco router can do) doesn't mean I like it. The more functions a box performs, the greater the likelihood that all of those functions will be performed at a mediocre level. Mediocrity is an improvement over zero security protection for some sites, but elsewhere it will not be sufficient.
I should say that the top diagram has its merits, with simplicity being the primary advantage. With so many networks having multiple "moving parts," it can be tough to stay operational and understand what's working or not working. Moving all those moving parts onto a single platform may not yield all the simplicity one might expect, however!
One way to address the weaknesses of these UTMs is to deploy stand-alone devices performing network forensics, so they record exactly what happens on the network. Using that data, one can investigate security incidents as well as measure the effectiveness of the UTM. I do not foresee network forensics collapsing into security switches/routers due to the data retention requirements and reconstruction workload required for investigations.
To survive I think network security inspection/interdiction vendors either need to be in the "meta-security" space (SIM/SEM) or in the do-it-all space (UTM). If your favorite vendor is in neither space, expect them to be acquired or go out of business.




Comments
UTM has some great advantages, but I would never want to have a single point of failure like that. Just imagine a bug in my virus scan (like the last clamav vulnerability), crashing my firewall, ids, mail scan and disrupting my whole network.
UTM's are good for small networks with a tight budget, but medium/large enteprises can't have a single point of failure like that..
*I didn't even mention defense in depth or privilege/process separation... :)
Daniel
I want to understand whether or not this perspective on "UTM" is an evolution of thinking on your part or a change of heart as it relates to the following statement you've made:
"It seems as though all network security functions are going to collapse into the devices which carry traffic -- switches."
...are you suggesting that switches are going to be(come) UTM devices? I've always understood your position to be quite literal in as much as ALL security will go into the switch and while Cisco may not call their products "UTM," devices such as the ASA are trending toward it.
Interesting comments, for sure.
@Daniel:
Not every UTM architecture suffers from the issues you describe. The market definition of "UTM" (the SME/SMB perimeter solutions) certainly fall into this space and these limitations.
Others, do not.
/Hoff
I see UTM as the last step before everything ends up in the switch. In the figure at the top, the end of the line will be the switches/routers and nothing else.
Do you have a bigger size UTM chart? I'm looking for it for quite some time now.
Pls email it to riconeo at gmail dot com
Thanks! :)
That's all I have. I suggest asking the magazine directly.