IATF Discusses Availability and Awareness
Yesterday I attended a meeting of the Information Assurance Technical Framework (IATF) Forum. I last attended an IATF meeting two years ago. According to this introduction (.pdf) document, the IATF Forum "is a National Security Agency (NSA) sponsored outreach activity created to foster dialog amongst U.S. Government agencies, U.S. Industry, and U.S. Academia seeking to provide their customers solutions for information assurance problems." Half of the attendees were government contractors, and a quarter were government civilians.
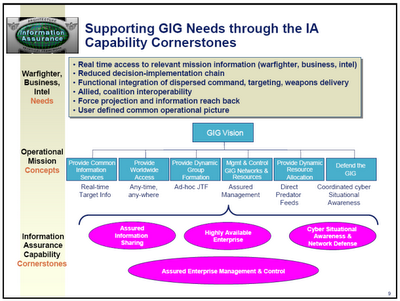
This meeting focused on two elements of the Information Assurance (IA) "cornerstones" DoD's Global Information Grid (GIG): the "Highly Available Enterprise" (HAE) and "Cyber Situational Awareness and Network Defense." (CSA/ND) The Government Accounting Office report The Global Information Grid and Challenges Facing Its Implementation (.pdf) provides a GIG overview. The NSA describes IA with respect to the GIG, and Craig Harber's December 2004 presentation The Information Assurance Component of the Global Information Grid (GIG) Integrated Architecture (.pdf) provides background on the IA cornerstones of the GIG. One slide from his presentation explains the four cornerstones:
The GIG is a long-term project, with deployment envisioned for 2020. This interview with NSA IA director Daniel G. Wolf explains NSA's role in the project and provides some information on GIG security initiatives.
One of the speakers yesterday works in the Joint Task Force Global Network Operations (JTF-GNO), which began life as the Joint Task Force Computer Network Defense (JTF-CND) when I was still in the Air Force. The JTF-GNO has a new security operations center, pictured at left and described in the article At the Heart of the Network. JTF-GNO also has a new commander; in July Air Force Lt Gen Charles E. Croom became director of the Defense Information Systems Agency (DISA) and commander of the JTF-GNO. I think it is a good idea that the person who owns DoD networks (DISA) is also in charge of defending them (JTF-GNO).
Military Information Technology magazine has a few other helpful articles on GIG and IA topics, like Global Network Guardians.
After deciphering all of the acronyms flying through the air, I found aspects of the meeting fascinating. For example, none of the CSA/ND speakers addressed network "intrusion prevention systems." Upon asking a panel about this issue, I learned there is interest in host-based "IPS", and research into determining if network IPS can be helpful.
One speaker from NSA, when describing his budget, said "IA is a hard sell... People do not fully appreciate the risk they are assuming." If even the .mil community doesn't appreciate network risks, what does that say about people with less sensitive information to protect?
To deal with limited resources, NSA is developing intellectual property that it will transfer to commercial vendors. The vendors will then sell finished products back to NSA. This is a cost-saving alternative to the traditional procurement strategy, where NSA designs, builds, and fields equipment completely in-house. To implement this plan NSA is trying to incorporate Internet standards into its own designs (like subsets of IPSec) while participating in the development of new standards.
One of the CSA/ND speakers noted that a study done 18 months ago found 20% of DoD bandwidth was used by unauthorized peer-to-peer file sharing applications. DoD has since taken steps to reduce and eliminate this traffic, since DoD sees it as illegal and a means to introduce malicious code into the enterprise. No one asked about legitimate p2p applications like retrieving OS .iso's via BitTorrent.
Another speaker noted the important of monitoring. He said DoD conducts "policy monitoring to verify its guards operate as expected." This is exactly the right attitude. Prevention is well and good, but monitoring but always be performed to determine if prevention methods are operating properly. Failure detection cannot be performed by the system deployed to prevent intrusions. I am glad the DoD "gets" this.
Finally, one speaker said "DoD can no longer just download Snort." That really shocked me, although I should not have been surprised. Another speaker said his biggest obstacle was getting 57 separate DoD services, agencies, and organizations to implement security properly and report their status. 57! No one thinks of DoD much beyond the four services, but there are many DoD components that act independently.
The next conference is scheduled for 12 October 2005 and will discuss "Managing and Controlling Enterprise Security." I may be teaching in California that week, so I don't plan to attend.
This meeting focused on two elements of the Information Assurance (IA) "cornerstones" DoD's Global Information Grid (GIG): the "Highly Available Enterprise" (HAE) and "Cyber Situational Awareness and Network Defense." (CSA/ND) The Government Accounting Office report The Global Information Grid and Challenges Facing Its Implementation (.pdf) provides a GIG overview. The NSA describes IA with respect to the GIG, and Craig Harber's December 2004 presentation The Information Assurance Component of the Global Information Grid (GIG) Integrated Architecture (.pdf) provides background on the IA cornerstones of the GIG. One slide from his presentation explains the four cornerstones:
The GIG is a long-term project, with deployment envisioned for 2020. This interview with NSA IA director Daniel G. Wolf explains NSA's role in the project and provides some information on GIG security initiatives.
One of the speakers yesterday works in the Joint Task Force Global Network Operations (JTF-GNO), which began life as the Joint Task Force Computer Network Defense (JTF-CND) when I was still in the Air Force. The JTF-GNO has a new security operations center, pictured at left and described in the article At the Heart of the Network. JTF-GNO also has a new commander; in July Air Force Lt Gen Charles E. Croom became director of the Defense Information Systems Agency (DISA) and commander of the JTF-GNO. I think it is a good idea that the person who owns DoD networks (DISA) is also in charge of defending them (JTF-GNO).
Military Information Technology magazine has a few other helpful articles on GIG and IA topics, like Global Network Guardians.
After deciphering all of the acronyms flying through the air, I found aspects of the meeting fascinating. For example, none of the CSA/ND speakers addressed network "intrusion prevention systems." Upon asking a panel about this issue, I learned there is interest in host-based "IPS", and research into determining if network IPS can be helpful.
One speaker from NSA, when describing his budget, said "IA is a hard sell... People do not fully appreciate the risk they are assuming." If even the .mil community doesn't appreciate network risks, what does that say about people with less sensitive information to protect?
To deal with limited resources, NSA is developing intellectual property that it will transfer to commercial vendors. The vendors will then sell finished products back to NSA. This is a cost-saving alternative to the traditional procurement strategy, where NSA designs, builds, and fields equipment completely in-house. To implement this plan NSA is trying to incorporate Internet standards into its own designs (like subsets of IPSec) while participating in the development of new standards.
One of the CSA/ND speakers noted that a study done 18 months ago found 20% of DoD bandwidth was used by unauthorized peer-to-peer file sharing applications. DoD has since taken steps to reduce and eliminate this traffic, since DoD sees it as illegal and a means to introduce malicious code into the enterprise. No one asked about legitimate p2p applications like retrieving OS .iso's via BitTorrent.
Another speaker noted the important of monitoring. He said DoD conducts "policy monitoring to verify its guards operate as expected." This is exactly the right attitude. Prevention is well and good, but monitoring but always be performed to determine if prevention methods are operating properly. Failure detection cannot be performed by the system deployed to prevent intrusions. I am glad the DoD "gets" this.
Finally, one speaker said "DoD can no longer just download Snort." That really shocked me, although I should not have been surprised. Another speaker said his biggest obstacle was getting 57 separate DoD services, agencies, and organizations to implement security properly and report their status. 57! No one thinks of DoD much beyond the four services, but there are many DoD components that act independently.
The next conference is scheduled for 12 October 2005 and will discuss "Managing and Controlling Enterprise Security." I may be teaching in California that week, so I don't plan to attend.



Comments
Interest read. They went from JTF-CND to JTF-CNO (Computer Network Operations) before I had left. I guess it ties in with their whole "global unification" stragedy within the DoD community.
As far as legitimate p2p applications, I would seriously doubt it. I know there are some out there, but most likely only locally approved by the DAA. I would say especially so about downloading OS .iso's. Each operating system has to be approved, regardless if it's a minor change. It took us three years to get FreeBSD approved for sensors to go out to bases, and that's only one version of the OS.
Snort has always been the bastard child to the DoD. It has been so because most organizations wouldn't monitor or tune the IDS. I guess they believed that having the IDS was security enough. Not only that, but they want to align IDS monitoring to a more standardized way. Somewhat like the push for JSIM or whatever the name for the Joint IDS was.
Sean
Stragedy -- strategy
English is fun.