Plugins for Firebird
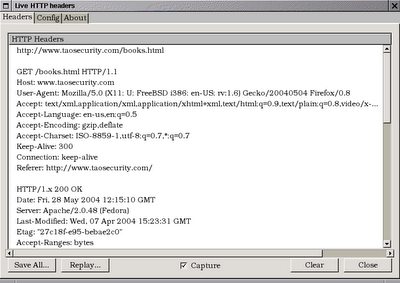
Don't care to see Macromedia Flash on Web sites while using Firefox ? Try installing Flashblock . You can install the .xpi file as a user and have it work at sites like Tom's Hardware as soon as you restart Firefox. Another cool plugin for Firebird (or Mozilla for that matter) is Live HTTP Headers . You can use this plugin to watch your browser's HTTP requests and the server's HTTP responses. To install this plugin, change the permissions on your /usr/X11R6/lib/firefox/lib/mozilla-1.6/components and /usr/X11R6/lib/firefox/lib/mozilla-1.6/chrome directories to be writable by the user installing the plugin. Alternatively, run Firefox as root and then install the plugin. Update : Check out the Web Developer Firefox extension. It's incredibly powerful.



