Continuous Diagnostic Monitoring Does Not Detect Hackers
There is a dangerous misconception coloring the digital security debate in the Federal government. During the last week, in the wake of the breach at the Office of Personnel Management (OPM), I have been discussing countermeasures with many parties. Concerned officials, staffers, and media have asked me about the Einstein and Continuous Diagnostic Monitoring (CDM) programs. It has become abundantly clear to me that there is a fundamental misunderstanding about the nature of CDM. This post seeks to remedy that problem.
The story Federal cyber protection knocked as outdated, behind schedule by Cory Bennett unfortunately encapsulates the misunderstanding about Einstein and CDM:
The main system used by the federal government to protect sensitive data from hacks has been plagued by delays and criticism that it is already outdated — months before it is even fully implemented.
The Einstein system is intended to repel cyberattacks like the one revealed last week by the Office of Personnel Management (OPM)...
Critics say Einstein has been a multibillion-dollar boondoggle that is diverting attention away from the security overhaul that is needed...
To offset those shortcomings, officials in recent years started rolling out a Continuous Diagnostics and Mitigation (CDM) program, which searches for nefarious actors once they’re already in the networks. It’s meant to complement and eventually integrate with Einstein. (emphasis added)
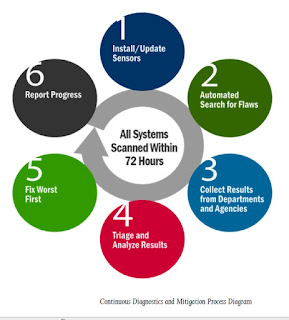
The section I bolded and underlined is 100% false. CDM does not "search" for "nefarious actors" "in the networks." CDM is a vulnerability management program. Please see the figure at the upper left. It depicts the six phases of the CDM program:
Don't misunderstand my criticism of CDM as praise for Einstein. At the very least, Einstein, or a technology like it, should have been deployed across the Federal government while I was still in uniform, 15 years ago. We had equivalent technology in the Air Force 20 years ago. (See the foreword for my latest book online for history.)
Furthermore, I'm not saying that CDM is a bad approach. All of the CDM phases are needed. I understand that intruders are going to have an easy time getting back into a poorly secured network.
My goal with this post is to show that CDM is either being sold as, or misunderstood as, a way to detect intruders. CDM is not an intrusion detection program; CDM is a vulnerability management program, a method to Find and Fix Flaws Faster. CDM should have been called "F^4, F4, or 4F" to capture this strategic approach.
The focus on CDM has meant intruders already present in Federal networks are left to steal and fortify their positions, while scarce IT resources are devoted to patching. The Feds are identifying and locking doors and windows while intruders are inside the house.
It's time for a new (yet ideologically very old) strategy: find the intruders in the network, remove them, and then conduct counter-intrusion campaigns to stop them from accomplishing their mission when they inevitably return. CDM is the real "multibillion-dollar boondoggle that is diverting attention away from the security overhaul that is needed." The OPM breach is only the latest consequence of the misguided CDM-centric strategy.
Tweet
The story Federal cyber protection knocked as outdated, behind schedule by Cory Bennett unfortunately encapsulates the misunderstanding about Einstein and CDM:
The main system used by the federal government to protect sensitive data from hacks has been plagued by delays and criticism that it is already outdated — months before it is even fully implemented.
The Einstein system is intended to repel cyberattacks like the one revealed last week by the Office of Personnel Management (OPM)...
Critics say Einstein has been a multibillion-dollar boondoggle that is diverting attention away from the security overhaul that is needed...
To offset those shortcomings, officials in recent years started rolling out a Continuous Diagnostics and Mitigation (CDM) program, which searches for nefarious actors once they’re already in the networks. It’s meant to complement and eventually integrate with Einstein. (emphasis added)
The section I bolded and underlined is 100% false. CDM does not "search" for "nefarious actors" "in the networks." CDM is a vulnerability management program. Please see the figure at the upper left. It depicts the six phases of the CDM program:
- Install/update "sensors." (More on this shortly)
- Automated search for flaws.
- Collect results from departments and agencies.
- Triage and analyze results.
- Fix worst flaws.
- Report progress.
CDM searches for flaws (i.e., vulnerabilities), and Federal IT workers are supposed to then fix the flaws. The "sensors" mentioned in step 1 are vulnerability management and discovery platforms. They are not searching for intruders. You could be forgiven for misunderstanding what "sensor" means. Consider the following from the DHS CDM page:
The CDM program enables government entities to expand their continuous diagnostic capabilities by increasing their network sensor capacity, automating sensor collections, and prioritizing risk alerts.
Again, "sensor" here does not mean "sensing" to find intruders. The next paragraph says:
CDM offers commercial off-the-shelf (COTS) tools, with robust terms for technical modernization as threats change. First, agency-installed sensors perform an automated search for known cyber flaws. Results feed into a local dashboard that produces customized reports, alerting network managers to their worst and most critical cyber risks based on standardized and weighted risk scores. Prioritized alerts enable agencies to efficiently allocate resources based on the severity of the risk. Progress reports track results, which can be used to compare security posture among department/agency networks. Summary information can feed into an enterprise-level dashboard to inform and situational awareness into cybersecurity risk posture across the federal government.
The "situational awareness" here means configuration and patch status, not intrusion status.
I captured the CMD figure from US-CERT's Continuous Diagnostic Monitoring program overview (pdf). It also appears on the DHS CDM page. The US-CERT program Web page lists the core tools used for CDM as the following:
- Intro to Hardware Asset Management (HWAM)
- Intro to Software Asset Management (SWAM)
- Intro to Vulnerability Management (VUL)
- Intro to Configuration Settings Management (CSM)
As you can see, CDM is about managing infrastructure, not detecting and responding to intruders. Don't be fooled by the "monitoring" in the term CDM; "monitoring" here means looking for flaws.
In contrast, Einstein is an intrusion detection and prevention platform. It is a network-based system that uses threat signatures to identify indications of compromise observable in network traffic. Einstein 1 and 2 were more like traditional IDS technologies, while Einstein 3 and 3 accelerated are more like IDP technologies.
Critics of my characterization might say "CDM is more than faster patching." According to the GSA page on CDM, CDM as I described earlier is only phase 1:
Endpoint Integrity
- HWAM – Hardware Asset Management
- SWAM – Software Asset Management
- CSM – Configuration Settings Management
- VUL – Vulnerability Management
Phase 2 will include the following:
Least Privilege and Infrastructure Integrity
- TRUST –Access Control Management (Trust in People Granted Access)
- BEHAVE – Security-Related Behavior Management
- CRED – Credentials and Authentication Management
- PRIV – Privileges
Phase 3 will include the following:
Boundary Protection and Event Management for Managing the Security Lifecycle
- Plan for Events
- Respond to Events
- Generic Audit/Monitoring
- Document Requirements, Policy, etc.
- Quality Management
- Risk Management
- Boundary Protection – Network, Physical, Virtual
What do you not see listed in any of these phases? Aside from "respond to events," which does not appear to mean intrusions, I still see no strong focus on detecting and responding to intrusions. CDM beyond phase 1 is still just dealing with "cyber hygiene." Unfortunately, even the President does not have the proper strategic focus. As reported by the Hill:
President Obama acknowledged that one of the United States’s problems is that it has a “very old system.”
“What we are doing is going agency by agency and figuring out what can we fix with better practices and better computer hygiene by personnel, and where do we need new systems and new infrastructure in order to protect information,”Don't misunderstand my criticism of CDM as praise for Einstein. At the very least, Einstein, or a technology like it, should have been deployed across the Federal government while I was still in uniform, 15 years ago. We had equivalent technology in the Air Force 20 years ago. (See the foreword for my latest book online for history.)
Furthermore, I'm not saying that CDM is a bad approach. All of the CDM phases are needed. I understand that intruders are going to have an easy time getting back into a poorly secured network.
My goal with this post is to show that CDM is either being sold as, or misunderstood as, a way to detect intruders. CDM is not an intrusion detection program; CDM is a vulnerability management program, a method to Find and Fix Flaws Faster. CDM should have been called "F^4, F4, or 4F" to capture this strategic approach.
The focus on CDM has meant intruders already present in Federal networks are left to steal and fortify their positions, while scarce IT resources are devoted to patching. The Feds are identifying and locking doors and windows while intruders are inside the house.
It's time for a new (yet ideologically very old) strategy: find the intruders in the network, remove them, and then conduct counter-intrusion campaigns to stop them from accomplishing their mission when they inevitably return. CDM is the real "multibillion-dollar boondoggle that is diverting attention away from the security overhaul that is needed." The OPM breach is only the latest consequence of the misguided CDM-centric strategy.
Tweet



Comments
From a model perspective, ATT&CK; for the framework, CAR / CARET -- https://car.mitre.org/caret/; and for the platform: either Cobalt Strike Malleable C2 and/or PowerShellEmpire Communication Profiles -- https://bluescreenofjeff.com/2017-03-01-how-to-make-communication-profiles-for-empire/ -- ? Wasn't this the foundation for programs such as the Fort Meade eXperiment (FMX) -- https://www.mitre.org/careers/working-at-mitre/employee-voices/a-cyber-security-engineer-scores-a-big-win-with-attck -- ?
I would say that CDM holds up given this set of inputs, subject of course, to other measured criteria. One of the criteria that I would add to ATT&CK and CAR / CARET would be characterization of initial-entry points, whether by social engineering (e.g., cred theft via unintentional insider), trusted insider, and/or exploitation (e.g., by CVE and/or attack vector, i.e., http://tecapi.com ). CARET, in particular, seems to be focused on access-expansion techniques, but not initial-entry points.