My Security Strategy: The "Third Way"

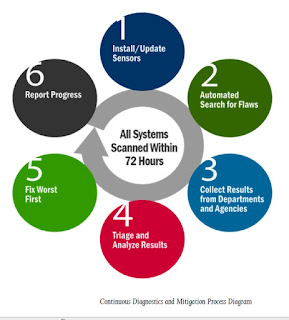
Over the last two weeks I listened to and watched all of the hearings related to the OPM breach. During the exchanges between the witnesses and legislators, I noticed several themes. One presented the situation facing OPM (and other Federal agencies) as confronting the following choice: You can either 1) "secure your network," which is very difficult and going to "take years," due to "years of insufficient investment," or 2) suffer intrusions and breaches, which is what happened to OPM. This struck me as an odd dichotomy. The reasoning appeared to be that because OPM did not make "sufficient investment" in security, a breach was the result. In other words, if OPM had "sufficiently invested" in security, they would not have suffered a breach. I do not see the situation in this way, for two main reasons. First, there is a difference between an "intrusion" and a "breach." An intrusion is unauthorized access ...