2006 CSI-FBI Study Confirms Insider Threat Post
Earlier this week I said Of Course Insiders Cause Fewer Security Incidents. I'm taking heat over at Matasano, but I've got some fresh facts to back me up, after getting a pointer from this Dark Reading story. In short, the 2006 CSI-FBI study is now available, and it confirms my proposition.
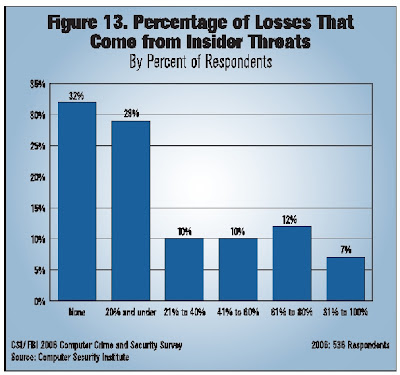
The study shows there is a new significance for the number "80%". Check out this chart from page 13. If you add up the two left columns, it shows that a clear majority of survey respondents -- 61% -- believe that "none" or 20% or less of their losses come from insiders. In other words, for the clear majority of survey respondents, 80% or more of their losses come from external threats.
Why is this? Apparently it's caused by the number one cause of dollar losses -- "virus contamination." "Unauthorized access to information" is a fairly close second, compared to the positions of the other dollar losses. It's interesting that "system penetration by outsider" accounts for a fraction of losses -- but maybe external attackers gaining "unauthorized access to information" is the problem? It's probably not insiders gaining "unauthorized access to information," since (1) most insiders already have access -- they just misuse it; and (2) if insiders were such a problem, they would account for a bigger proportion of losses.
Again, again -- I agree that insiders have the potential to cause the biggest amount of damage. Look at the havoc caused by rogue CEOs and CFOs. However, the numbers aren't lying -- external problems are bigger. We have ways of dealing with rogue insiders that completely dwawf our options with handling outsiders.
At some point my critics will recognize the reason I am so vocal about the difference between threats and vulnerabilities. For the most part, we can address vulnerabilities. Secure coding, security infrastructure, configuration management, training, etc. all help reduce the number of vulnerabilities (or at least have the potential to). After all, we control what we deploy (or at least we should!)
Threats are completely different. Threats are people, people living in basements in Eastern Europe, China, Africa, wherever -- outside the reach of law enforcement and the military. While we patch and configure away old vulnerabilities, these same external intruders never stop.
Behind every virus, Trojan, worm, botnet is a person -- a person -- yet we continue to worry about the latest hole in the Linux kernel. The only group who can make any difference in this battle against bad people are the police and military. Unfortunately, the current police and military infrastructure is currently not capable of addressing these threats.
We are not going to code, configure, or patch our way out of this problem, because the real issue is the threat, not the vulnerability. Vulnerabilities come and go; at present, threats continue until they get bored.
The study shows there is a new significance for the number "80%". Check out this chart from page 13. If you add up the two left columns, it shows that a clear majority of survey respondents -- 61% -- believe that "none" or 20% or less of their losses come from insiders. In other words, for the clear majority of survey respondents, 80% or more of their losses come from external threats.
Why is this? Apparently it's caused by the number one cause of dollar losses -- "virus contamination." "Unauthorized access to information" is a fairly close second, compared to the positions of the other dollar losses. It's interesting that "system penetration by outsider" accounts for a fraction of losses -- but maybe external attackers gaining "unauthorized access to information" is the problem? It's probably not insiders gaining "unauthorized access to information," since (1) most insiders already have access -- they just misuse it; and (2) if insiders were such a problem, they would account for a bigger proportion of losses.
Again, again -- I agree that insiders have the potential to cause the biggest amount of damage. Look at the havoc caused by rogue CEOs and CFOs. However, the numbers aren't lying -- external problems are bigger. We have ways of dealing with rogue insiders that completely dwawf our options with handling outsiders.
At some point my critics will recognize the reason I am so vocal about the difference between threats and vulnerabilities. For the most part, we can address vulnerabilities. Secure coding, security infrastructure, configuration management, training, etc. all help reduce the number of vulnerabilities (or at least have the potential to). After all, we control what we deploy (or at least we should!)
Threats are completely different. Threats are people, people living in basements in Eastern Europe, China, Africa, wherever -- outside the reach of law enforcement and the military. While we patch and configure away old vulnerabilities, these same external intruders never stop.
Behind every virus, Trojan, worm, botnet is a person -- a person -- yet we continue to worry about the latest hole in the Linux kernel. The only group who can make any difference in this battle against bad people are the police and military. Unfortunately, the current police and military infrastructure is currently not capable of addressing these threats.
We are not going to code, configure, or patch our way out of this problem, because the real issue is the threat, not the vulnerability. Vulnerabilities come and go; at present, threats continue until they get bored.



Comments
After all, there have been incidents recently that show that security incidents have gone completely unnoticed, some for as long as 13 months, such as this one.
Yes, I'm skeptical of the numbers, but right now they're the best numbers we have.
Harlan
There's no way to tell if those conclusions are factual, because the CSI/FBI survey does not permit statistical inferences about any population of interest (for example, US employers) to be drawn.
Regarding laptops, I don't know how that is counted.
Based upon the news reporting it seems that this is more 60/40 outside or even 50/50.
Has anyone done an Real analysis (and not just my perception) on the News to see how they are reporting it??? Would be interesting to see how it compares to this study.